Kaspersky says latest wave of Nigerian phishing scams are taking a more sinister turn
Nigerian phishing scams are so common as to become a popular meme. They inevitably revolve around human greed and involve emails that are sent out to potential victims, stating that they are the recipient of a massive amount of money or some such other lucrative deal before asking for personal details or a token but gradually increasing sum of money for a contrivance or another. Usually, these scams are out for money though recently they’re out to steal a different commodity from unsuspecting users and companies – information.
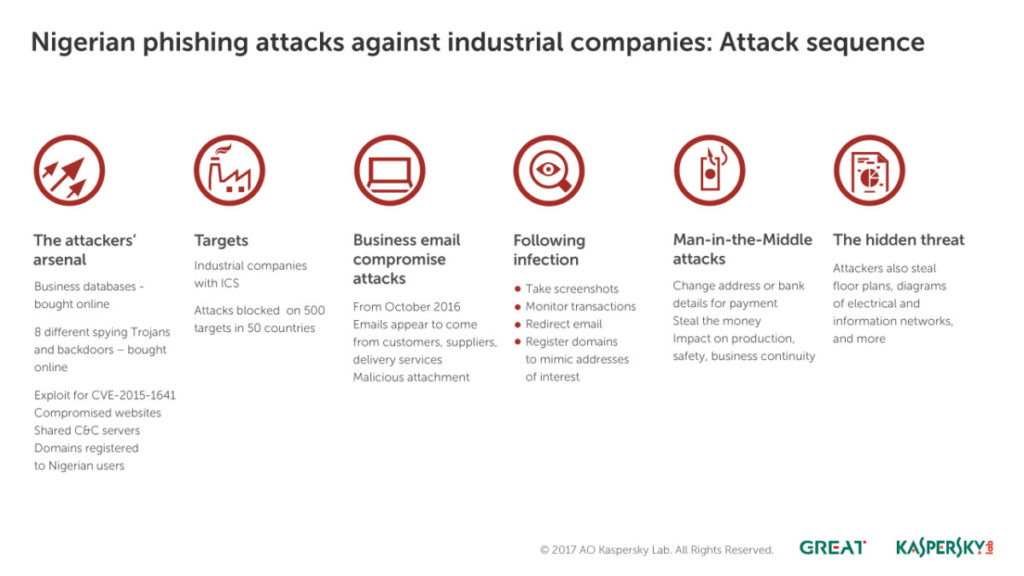
According to Kaspersky Lab’s Industrial Control Systems Cyber Emergency Response Team, there has a been a significant spike in malware infection attempts targeting industrial customers with over 500 attacked companies in 50 countries. These attacks seem focused on industrial enterprises, large transportation and logistic corporations and they’re still ongoing. These attacks aren’t just to intercept payments or to filch information to gain a competitive advantage. These attacks have made off with project and operational plans, diagrams of electrical and information networks and more. What they can potentially do with information of this nature is worrisome.
Do I know you?
Like most Nigerian phishing attack schemes, the first attacks come in the form of emails. Rather than a shotgun mass spam approach, these emails are carefully crafted to mimic legitimate correspondence from suppliers, customers and other business associates. Laced with these emails are off-the-shelf black market backdoor Trojans that compromise and infect systems in an attempt to steal data and install remote administration tools.
Once compromised, these corporate-owned computers are then used to monitor and redirect messages to the hacker’s own mailbox to determine potential avenues of attack. This is where things take a turn for the sinister. Rather than simply opting for plain old financial larceny, Kaspersky researchers noted that technical drawings and network diagrams were stolen which have no immediate financial value. Forensic research also noted that most of the domains used in the attacks were registered to Nigerian residents and that it is either one group behind all these attacks or several cooperating together.
“There is no need for the attackers to collect this kind of data in order to perpetrate their phishing scams. So what do they do with this information? Is the collection accidental or intentional – perhaps commissioned by a third party? So far, we have not seen any of the information stolen by Nigerian cybercriminals on the black market. However it is clear that, for the companies being attacked, in addition to the direct financial loss, a Nigerian phishing attack poses other, possibly more serious, threats,” said Maria Garnaeva, Senior Security Research, Critical Infrastructure Threat Analysis from Kaspersky Labs.