
Malaysia fifth most affected APAC country by cyberattacks in 2024 says Kaspersky cybersecurity threats 2024 report
At the Kaspersky Cybersecurity Weekend summit in Sri Lanka, the global cybersecurity company shared more about the cybersecurity threat landscape and the most dangerous threats for the year in their latest Kaspersky cybersecurity threats 2024 report.
Ironically, Malaysia is one of the countries in APAC that experienced the most cyberattacks for the duration of January – July 2024 with 31.4% of users affected though the most affected is the Philippines at 39.4% followed by Nepal at 36.8% and Sri Lanka at 34.9% with Malaysia being in fourth place and New Zealand trailing as the fifth most affected at 30.9%.

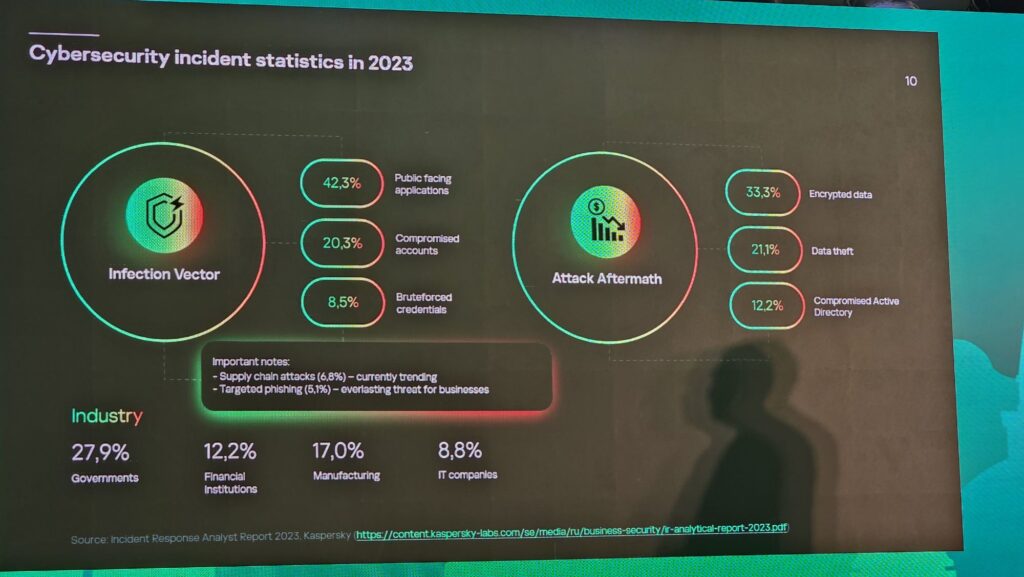
According to the most recent Kaspersky Incident Response Analyst Report 2023, 75% of cyberattack attempts exploited Microsoft Office while 42.3% of successful infection attempts use publicly available applications and 20.3% of successful attempts leverage compromised accounts.
Oddly enough, only 8.5% of successful attacks actually leverage the plain old brute force approach like dictionary attacks or simply spamming password combinations.
Further, Kaspersky added that most attacks involved using stolen or purchased credentials before committing a remote desktop protocol (RDP) attack, phishing emails with malicious attachments and malicious files on public resources. The aftermath of a cyberattack involves 33.3% of affected organisations got their data encrypted, 21.1% incurred data theft and 12.2% encountered compromised active directories.
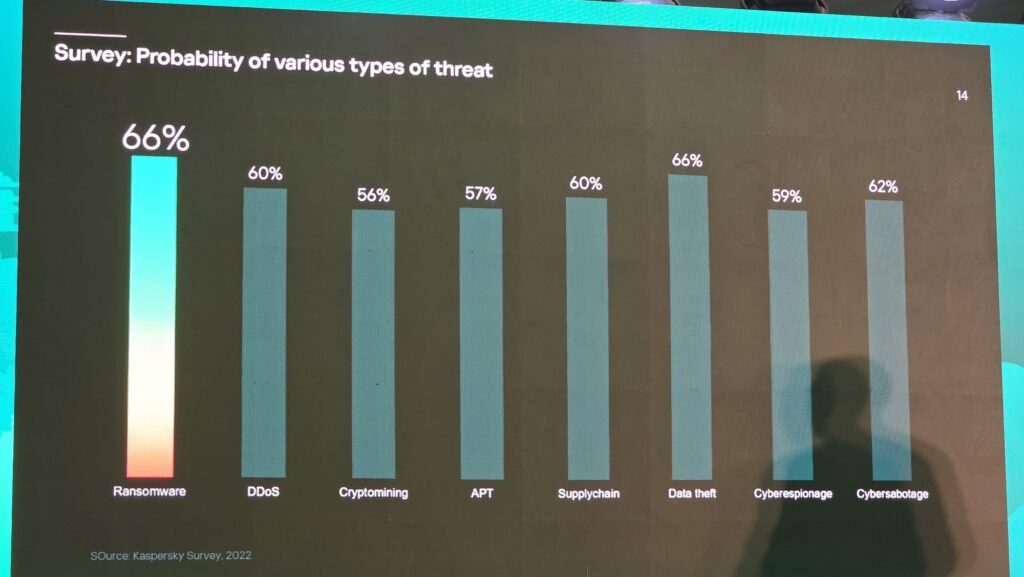
Based on another Kaspersky survey in 2022, the biggest cyberthreat is ransomware (66%) with data theft (66%), cybersabotage (62%), supply chain attacks (60%) and DDos attacks (60%), cyberespionage (59%), advanced persistent threats (APTs) 57% and cryptomining (56%). While the year is not yet out, 2024 the biggest emerging threats are supply chain attacks (6.8%) and phishing attempts (5.1%).
In 2023 statistics, the most popular target by threat actors was governments (27.9%), financial institutions (12.2%), manufacturing (17%) and IT companies (8.8%) with Asia and CIS seeing the most cybersecurity incidents at 47.3%, the Americas (21.8%), the Middle East (10.9%) and Europe (9.1%).
More recently, from January to July 2024, Kaspersky’ prevented 245 million web-borne threats, 340 million local threats were blocked, 2.76 million password stealers were detected, 1.29 million ransomware attacks were thwarted, 7.54 million backdoors in companies were detected and 62.9 million RDP attacks targeting businesses were prevented from doing so.
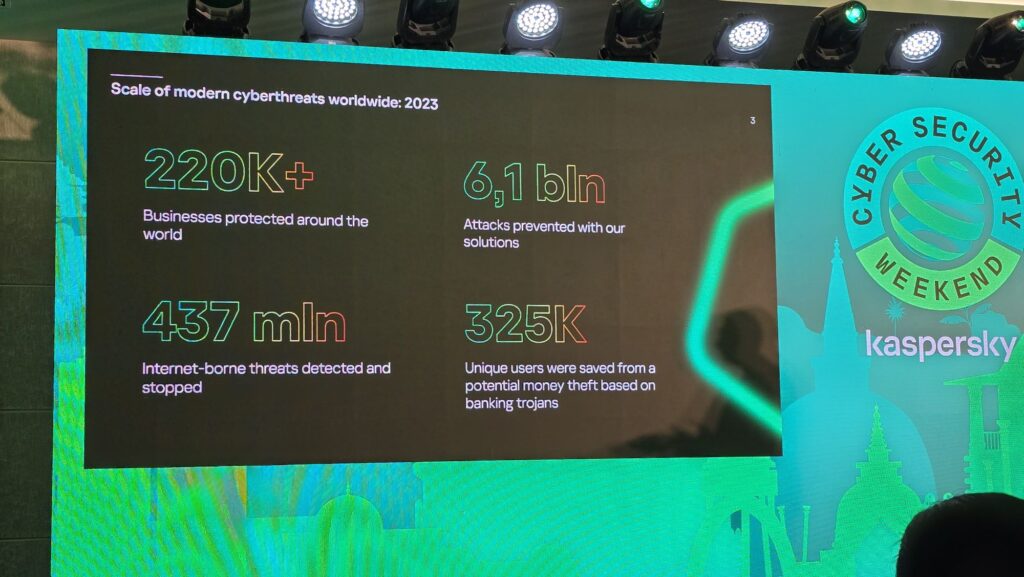
According to Kaspersky, 6.1 billion attacks were prevented with their security solutions with 437 million internet-borne threats detected and stopped with over 325,000 users protected from financial loss after banking trojans were detected and stopped in time.
Crime is a business – Ransomware as a service?
Another interesting fact shared at the Kaspersky Cybersecurity Weekend summit and their cybersecurity threats 2024 briefing was the fact that ransomware isn’t the case of a bunch of hackers in a basement doing it for laughs. These days, ransomware is now run as a business with 71% of detected cybersecurity incidents being financially driven with the number of organisations targeted by ransomware doubling in 2021-2022 with 68% of business owners believing that IT security risks keep rising.
“There are three popular myths in regards to ransomware,” said Igor,Kuznetsov, Director, Global Research & Analysis Team (GReAT) at Kaspersky. ”the first being that cybercriminals are just criminals with an IT education, that the targets of ransomware are set before an attack and ransomware gangs are acting along.” added Igor.
Among the highlights in the recent Kaspersky cybersecurity threats 2024 report was that ransomware is actually a performed as a service by cybercriminals
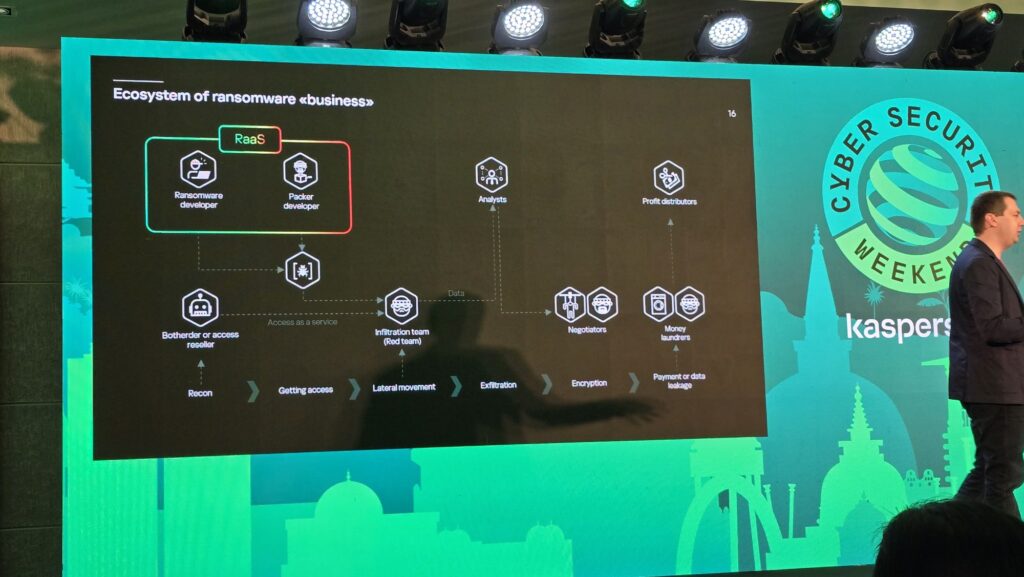
Much like a heist movie, ransomware as a service (RaaS) involves interacting with various criminal experts, typically starting off with a ransomware developer and a packer developer creating the malware itself before shopping it around to other cybercriminals and potential attackers purchasing entry to protected systems as a service, rogue analysts offering viable targets and professional negotiators to extort payment from victims.

Igor,Kuznetsov, Director, Global Research & Analysis Team (GReAT) at Kaspersky sharing more about how companies affected by ransomware should not pay the ransom and that Kaspersky maintains a large database of keys to counter these attempts in their recent summit where they also shared their latest cybersecurity threats 2024 report to the world
Ultimately, victims of ransomware must not pay the ransom. “Ultimately, affected organisations must not pay a ransom which will perpetuate and enable more cybercrime,” said Igor. He warned that even if a ransom is paid, the data may have already been stolen and could be leaked later or used for further extortion attempts. Instead, Igor highlighted alternative solutions: “Victims can often recover their data without paying. Kaspersky maintains a vault of keys and tools to decrypt data locked by various ransomware families. Since 2018, over 1.5 million users worldwide have successfully recovered their data using these resources.“
Cybersecurity threats 2024 -Operation Triangulation reveals iOS devices potential compromised and Containerised System risks
One of the most recent and most insidious cyberattacks revealed by Kaspersky showed that iOS devices were potentially vulnerable to intrusion. Designated as Operation Triangulation, the cyberattack uses highly sophisticated malware that uses four 0-day vulnerabilities to infect target devices and which would have cost more than US$1 million oni the back market to obtain.
The chain of attack involves a targeted iOS getting an invisible iMessage with a malicious attachment that installs itself undetected, contacts a server and then starts a multi-stage execution of a malware payload to get full control of the targeted device before all traces and logs are wiped to remove any traces of the attack.
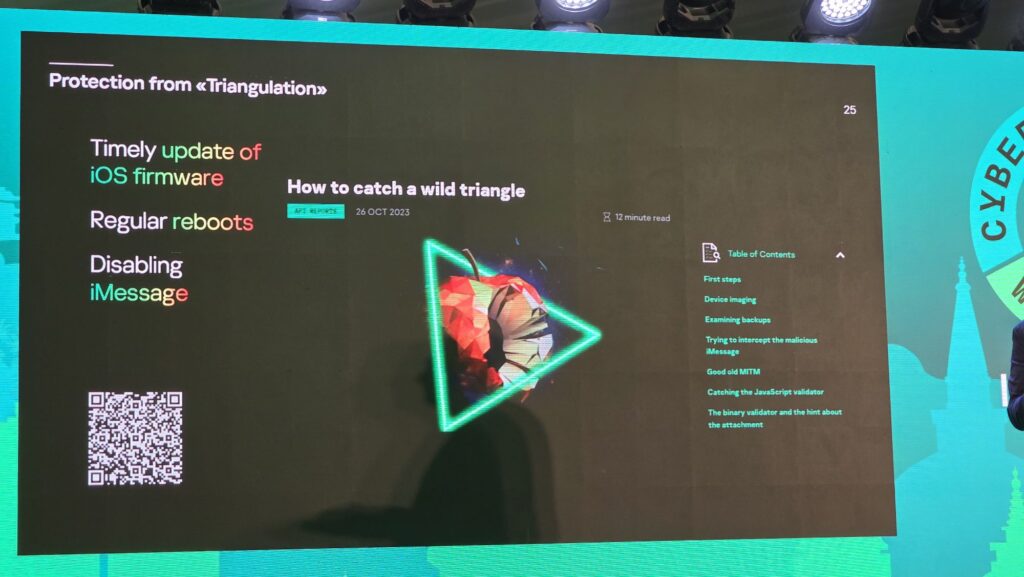
Another potential vector for cyberattacks are supply chain attacks tied to containerised systems running open-source software which rely on multiple third-party dependencies and which in turn introduces significant risks when exploited by threat actors.
While not caused intentionally, the recent Crowdstrike event caused over 8 million devices to display the blue screen of death and brought the world economy to a halt. Another potential attack was on XZ Utils, that was attacked via social engineering to install a potentially damaging payload that could have compromised millions of SSH-enabled devices.
For 2024, Kaspersky advises that organisations need to maintain a mature security posture through proper education of employees on cybersecurity risks, updated threat intelligence from trusted cybersecurity providers, regular operating system, application and antivirus software updates as well as employing security solutions like Kaspersky Endpoint Detection and Response.
For more details on Kaspersky Labs and cybersecurity threats 2024 highlights, check out www.kaspersky.com
